Copyright © 1E 2025 All Rights Reserved
OS Supported - Microsoft Windows, Microsoft Windows 11, 10
Description
This DEX Pack includes Endpoint Automation policies, rules, and instructions that empower end-users to temporarily elevate their permissions on their devices and also self-serve fixes to common issues.
Key Features
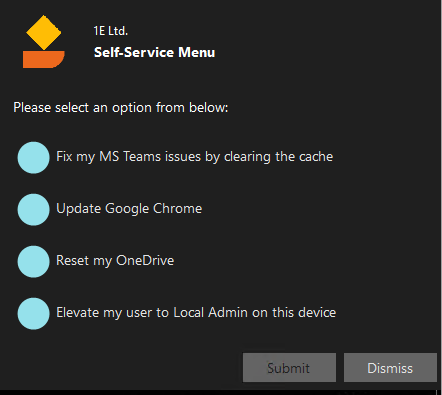
- End users can elevate their permissions to administrator level for a limited amount of time.
- Unauthorized elevations are logged, and any unauthorized changes are promptly undone.
- Configurable Self-Service fixes for common issues like MS teams, disk cache clean-up and reset Onedrive, etc.
Setup
- Upload this DEXPack with the help of the Product Pack Deployment Tool.
- An Endpoint Automation Policy named End-User Self-service pop-up will be created.
- Multiple Endpoint Automation rules will be created each prefixed with 'Self Service'.
- An Instruction Set named End-User Experience containing all the instructions will be created.
Pre-requisites for Azure AD (Below are the steps to be performed before deploying the DEX Pack only for administrator elevation. Generic Popup Options do not require Azure app registration.)
Step 1:- Create a new Microsoft 365 group or utilize an existing one to grant its members access to the option of elevating administrator rights on their devices.
Step 2 :- Create and register an Azure App in Microsoft Entra ID.
Step 3:- Provide the Microsoft Graph API Application permission Directory.Read.All and consent which will enable the registered app to read the group membership. List memberOf - Microsoft Graph v1.0 | Microsoft Learn
Step 4:- Add the Client secret and note it.
Step 5:- User survey functionality needs to be enabled on 1E clients.
Usage
For Azure AD, enable and configure the below shown rule:
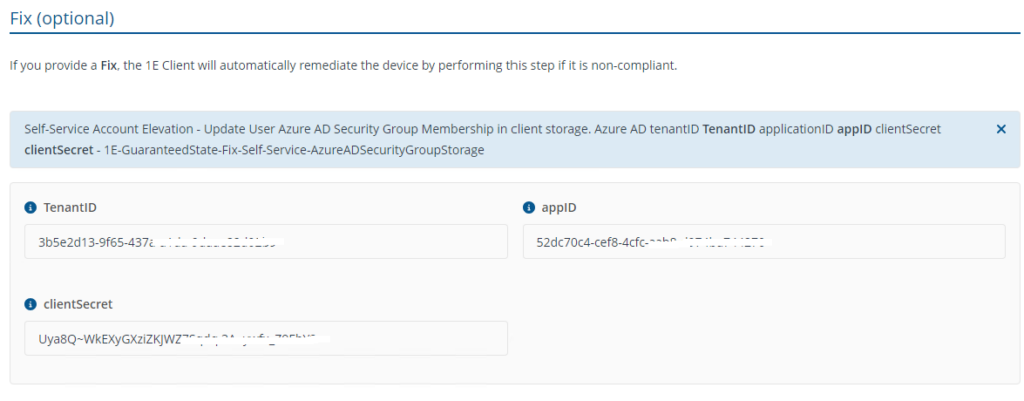
- Self-Service - Checks and Updates Azure AD group Memberships in storage
This rule will establish a local storage on the device, adding the group membership of the logged-in user. This feature enables the option to elevate admin rights. If the logged-in user is not a member of the specified Microsoft 365 group, they won't have the option to elevate to an administrator. In the Fix phase, include the Tenant ID, AppID, and ClientSecret registered earlier during the pre-requisite steps.
No configuration is required for Check rule.
NOTE: It's important to note that the endpoint should have internet access to fetch the Microsoft 365 group membership data.
For local AD, disable the rule for Azure AD and enable the below shown rule:
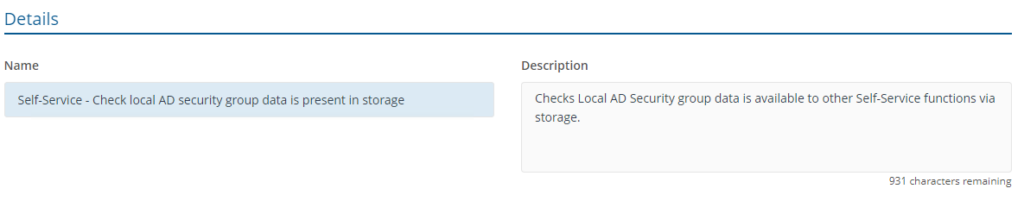
- Self-Service - Check local AD security group data is present in storage
This rule will check the group membership of the logged-in user and if the logged-in user is not a member of the specified local group, they won't have the option to elevate to an administrator.
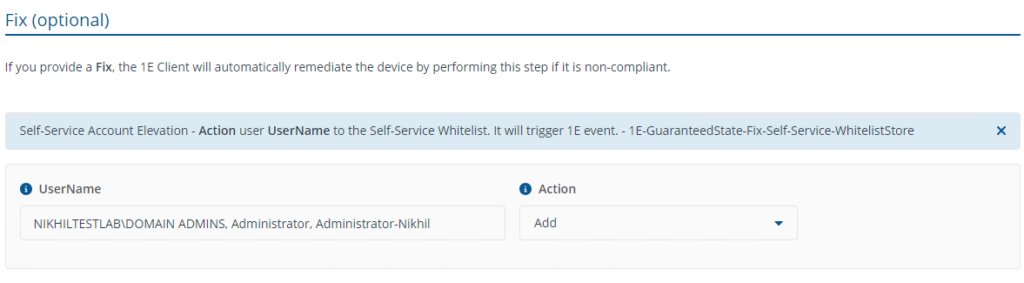
- Self-Service - Add Whitelist AD user
To implement this rule, configure the whitelist for specific users or groups, providing them with permanent administrator status on the device. Any additional users added to the administrator group will be automatically removed by the 'Self-Service - Remove unauthorized local admins' rule upon evaluation.
No configuration is required for Check.
- Self-Service - Deploy Icon to users
This rule will deploy a dummy exe and create a shortcut on the desktop which will provide the option to elevate the admin rights.
- Self-Service - PopUp options
This rule will only provide the GUI interface on end-user devices that are a member of the Microsoft 365 group or local AD group an option to elevate to an administrator, members that not a part of the group would not have an option to elevate the administrative rights. The Local Admin Security Group field should have the display name of the Microsoft 365 group for Azure AD or local AD Security group that will be used for evaluating group membership. Admin Popup Options should not be modified as it triggers the rule Self-Service - Elevate current user to Local Admin - Compliant which adds the user temporarily to the local administrator group.
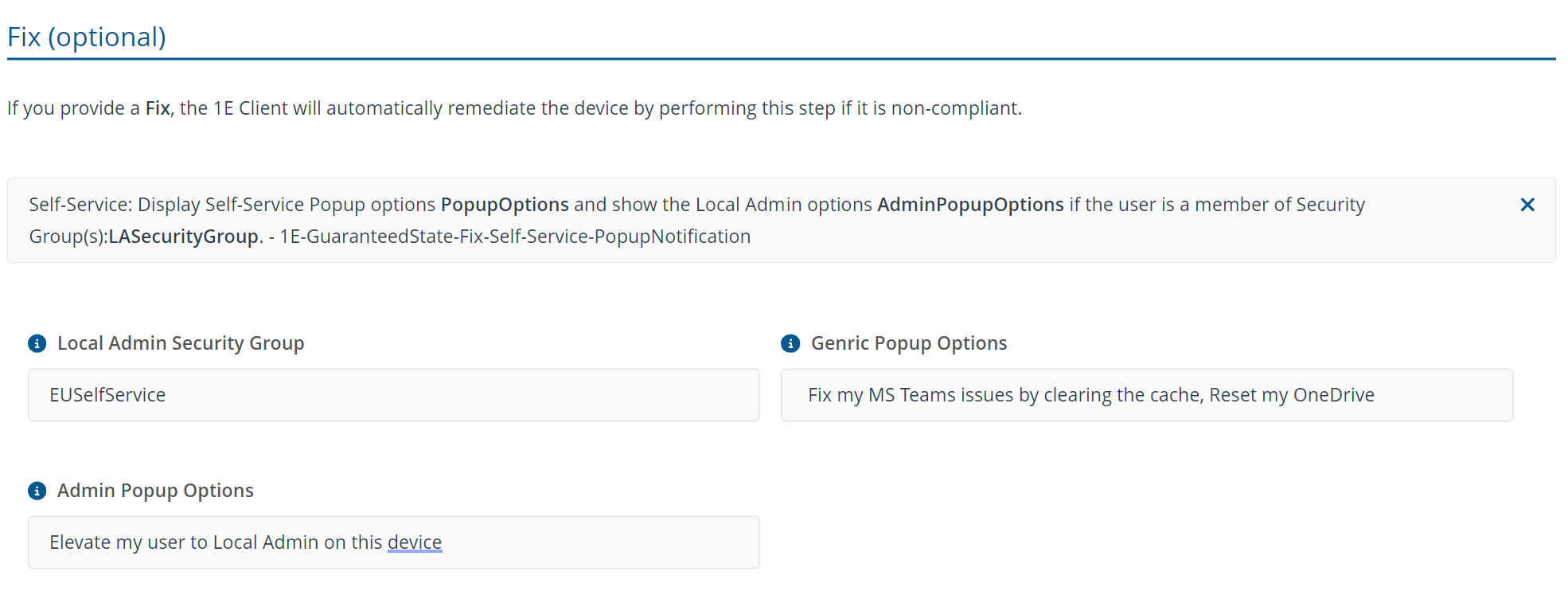
If the rule needs to be deployed without administrator elevation, then Local Admin Security Group and Admin Popup Options can be deployed with ‘None’ value and only the rules Self-Service - Deploy Icon to users and Self-Service - PopUp options need to be deployed.
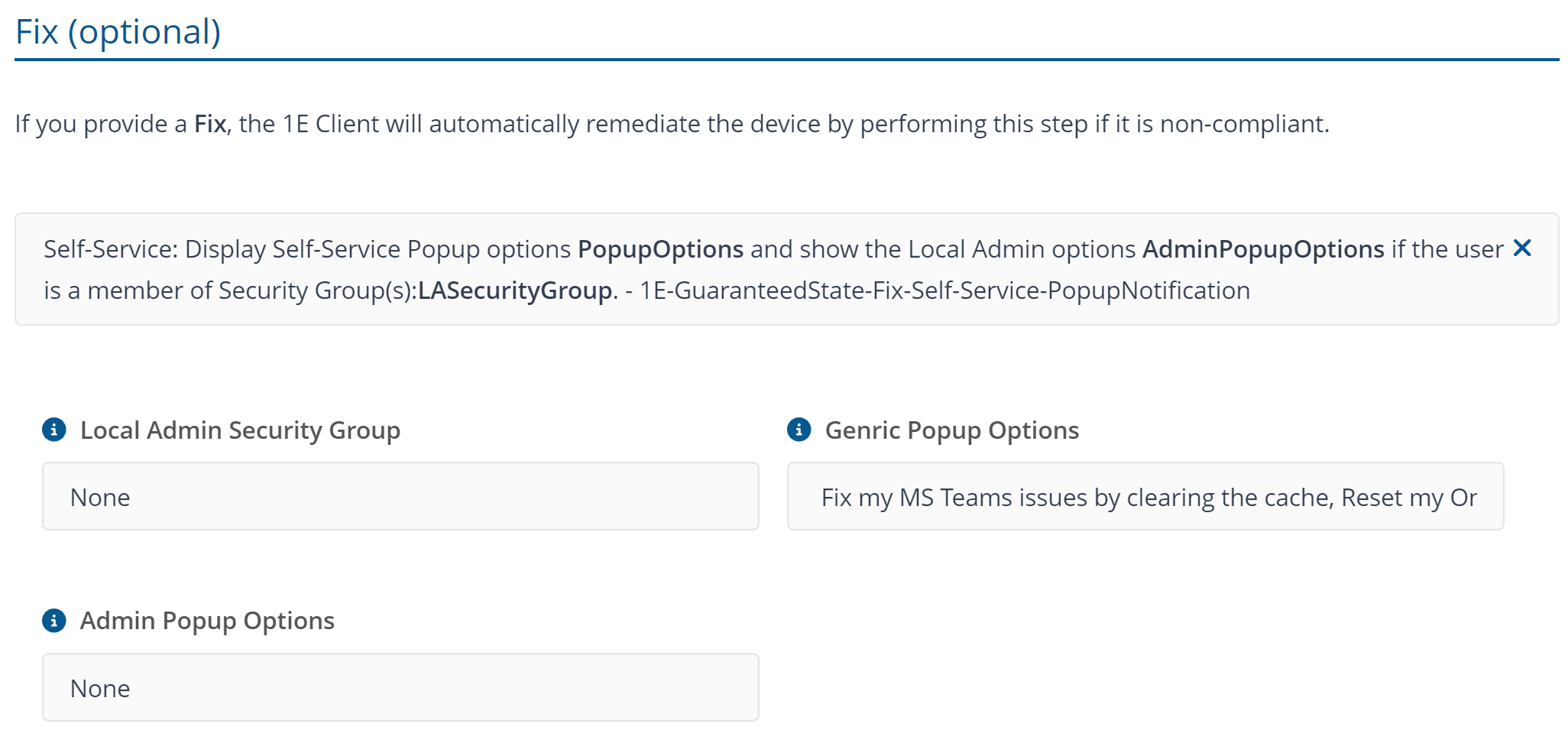
The 'Generic Popup Options' can be customized to trigger another Endpoint Automation rule, utilizing the topic as its trigger." Any other rule that needs to be triggered must use the trigger template A specified Tachyon event is triggered, a unique Topic name and check template Proceed to fix If rule RuleName is not triggered when 1E client service start or policy evaluated . The RuleName in check parameter must have the same name of the rule that will be trigger the fix forcefully and topic name needs to be applied in Generic Popup Options of the rule Self-Service - AAD options Popup. Use , (comma) to add multiple topic in Generic Popup Options.
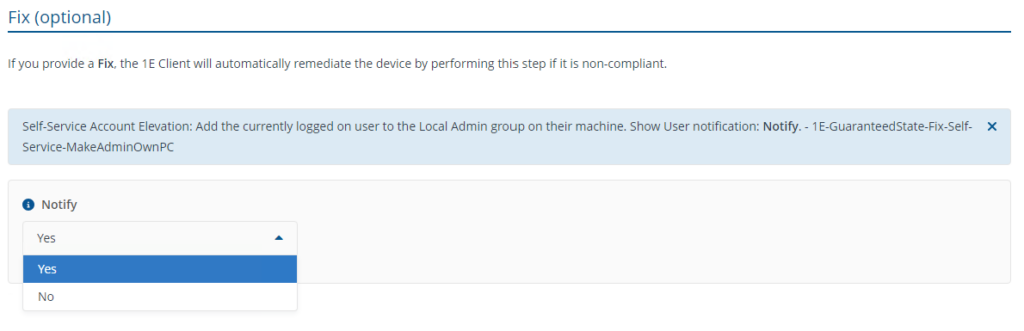
- Self-Service - Elevate current user to Local Admin - Compliant
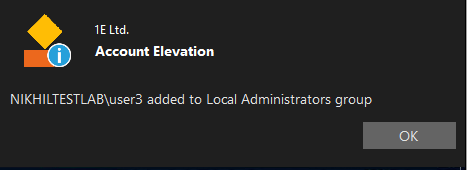
This rule adds the user temporarily to the local administrator group with an option to notify the user once the elevation is successful.
- Popup as shown below appears on end-user’s device to evaluate the administrator rights and generic options.
- Notification as shown below appears on the end-user's device after elevation is successful.
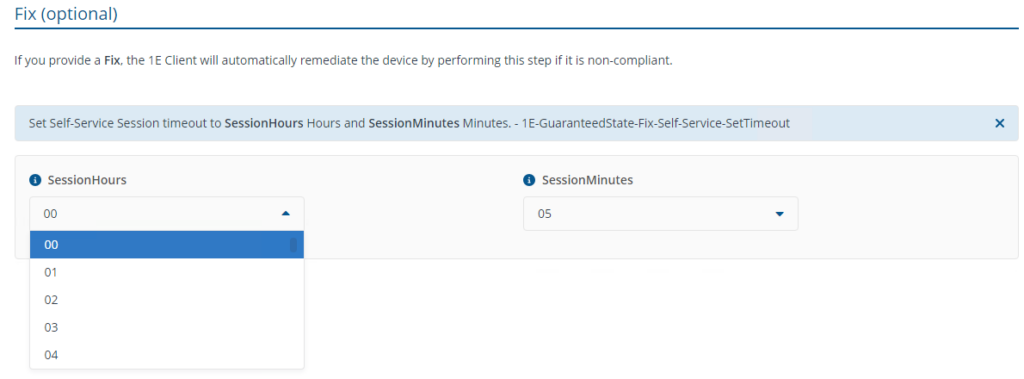
- Self-Service - Set Timeout Default
This rule configures the timeout period for the elevation of administrator rights.
- Self-Service - De-elevate user once elevation duration expires
This rule will automatically remove the elevated user once the timeout period has expired. There are no configurable components in this rule.
- Self-Service - Remove unauthorised local admins on log off
This rule will remove the elevated user from the local administrator group under the following conditions:
- Device restart
- Re-login
- Start-up after shutdown of the device.
- The end-user needs to re-elevate the rights.
The trigger utilizes the Windows security event log ID 4647.
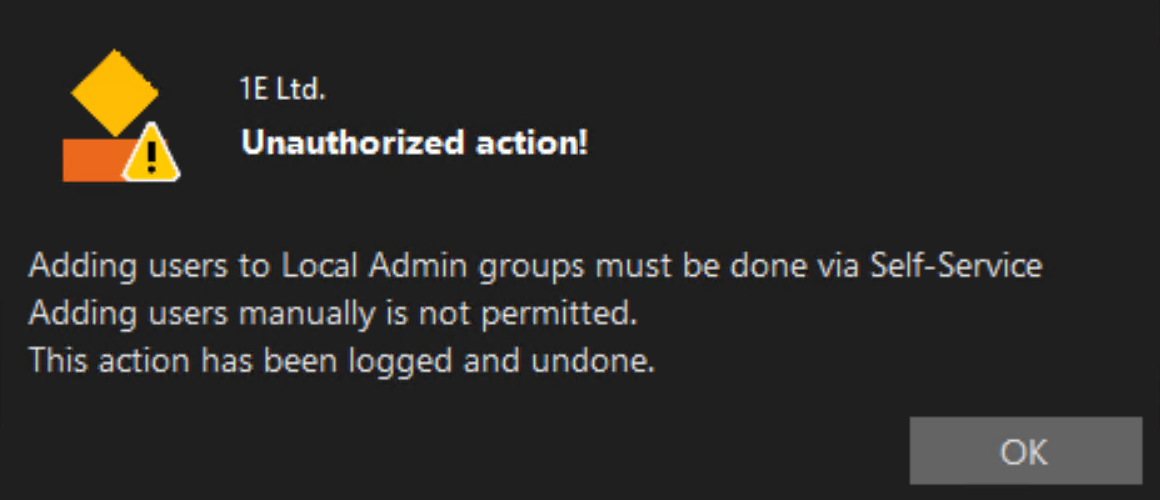
- Self-Service - Remove unauthorised local admins
This rule will remove the elevated user from the local administrators group on addition of a user to the local administrators group through methods other than the self-service approach. Once the device is enrolled to use self-service, any alternative methods used to add a non-whitelisted user to the local administrators group will be undone by this rule and logged into the audit logs which can be viewed by the instruction Group Self-Service Audit results by Trigger.
Below is the screenshot of the notification on end-user’s device upon detection of an Unauthorised attempt:
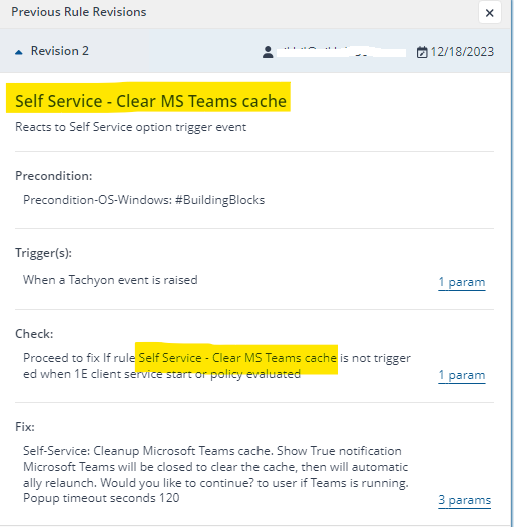
- Self Service - Clear MS Teams cache
This rule will trigger Microsoft teams cache clean-up once the end user select’s the option from the self service prompt and an option to provide a customized popup message.
Instructions
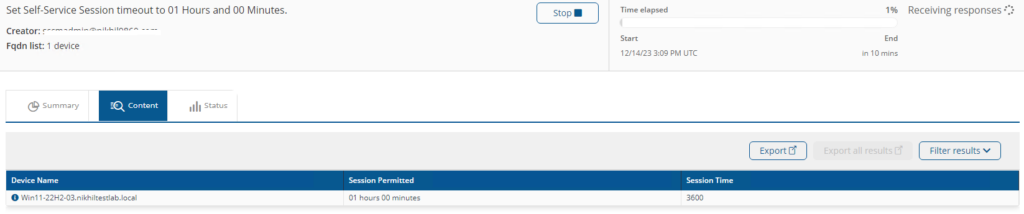
Set Self-Service Session timeout to <SessionHours> Hours and <SessionMinutes> Minutes.
This instruction will set the timeout period on a device for elevation but may get overridden by rule Self-Service - Set Timeout Default once the rule is trigged.
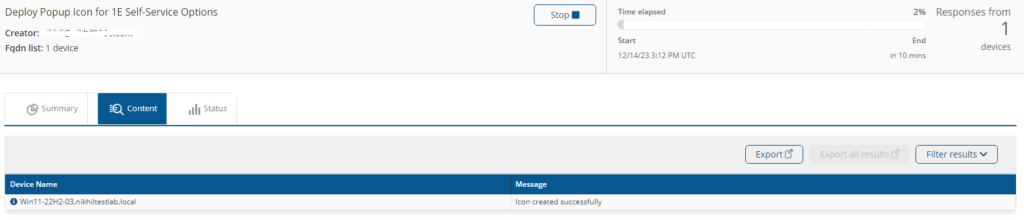
Deploy Popup Icon for 1E Self-Service Options
This instruction will Deploy the Self-Service EXE and icon on the device.
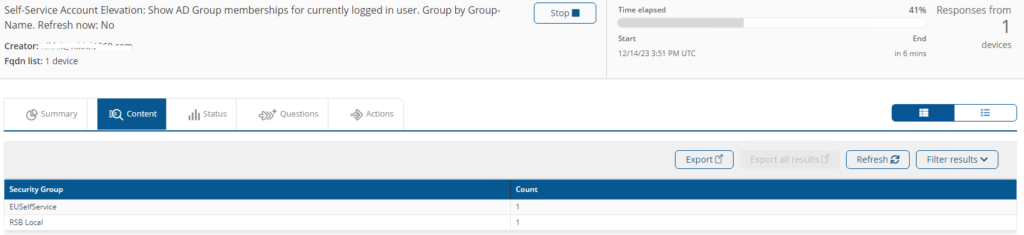
Self-Service Account Elevation: Show AD Group memberships for currently logged in user. Group by Group-Name. Refresh now: <Refresh>
This instruction will fetch the details of the AD group membership of the current logged in user and provides an option to refresh the membership.
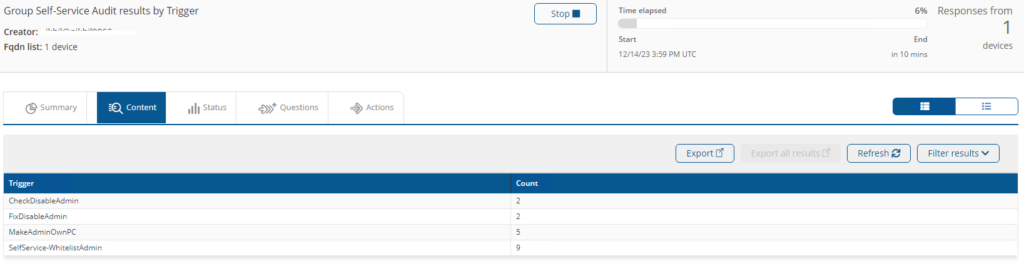
Group Self-Service Audit results by Trigger
This instruction will fetch the Audit logs that includes the elevation, de-elevation, whitelist action and unauthorized attempts.
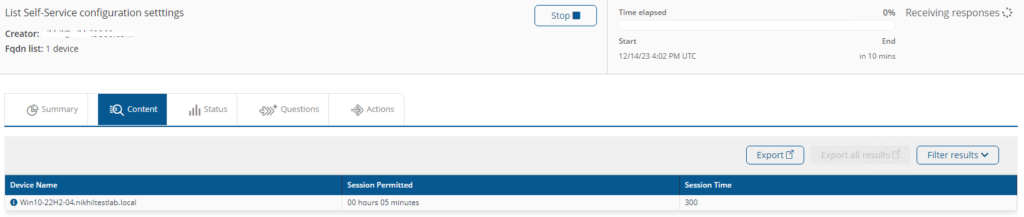
List Self-Service configuration settings
This instruction will fetch Self Service default timeout on the device.
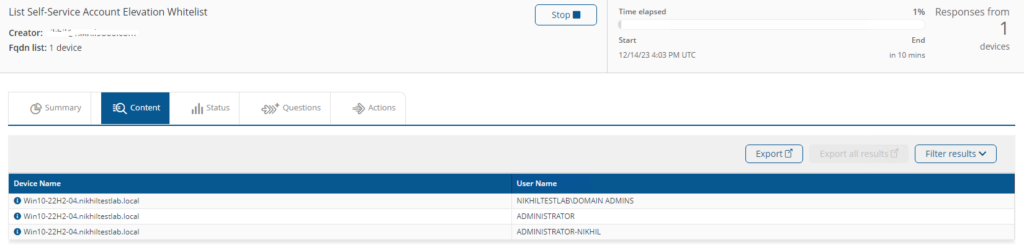
List Self-Service Account Elevation Whitelist
This instruction will fetch Whitelisted users account and groups from the Administrator’s group.
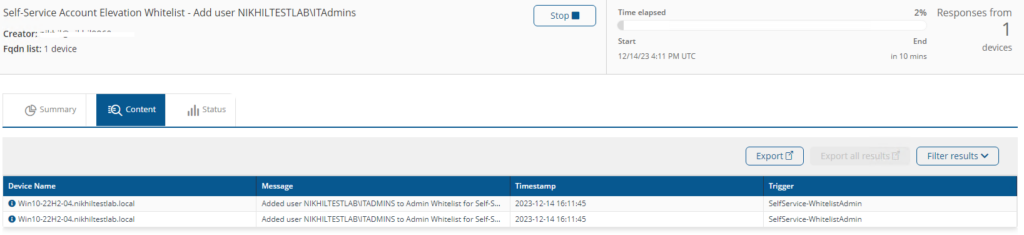
Self-Service Account Elevation Whitelist - <Action> user <UserName>
This instruction will Add/Remove the Whitelisting of users account and groups into the Administrator’s group.
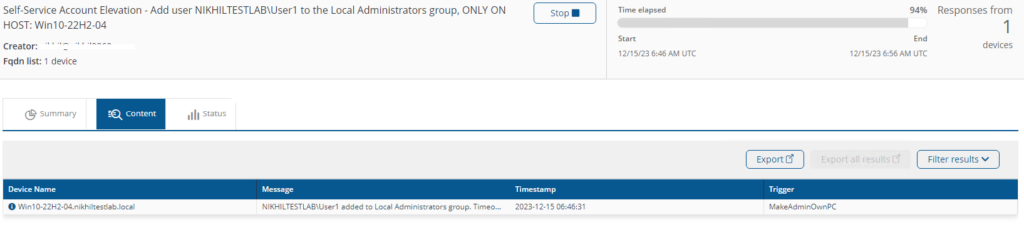
Self-Service Account Elevation - Add user <Username> to the Local Administrators group, ONLY ON HOST: <Hostname>
This instruction will temporarily elevate current user’s permission to administrator level on their devices for the defied period as per Self-Service - Set Timeout Default rule.
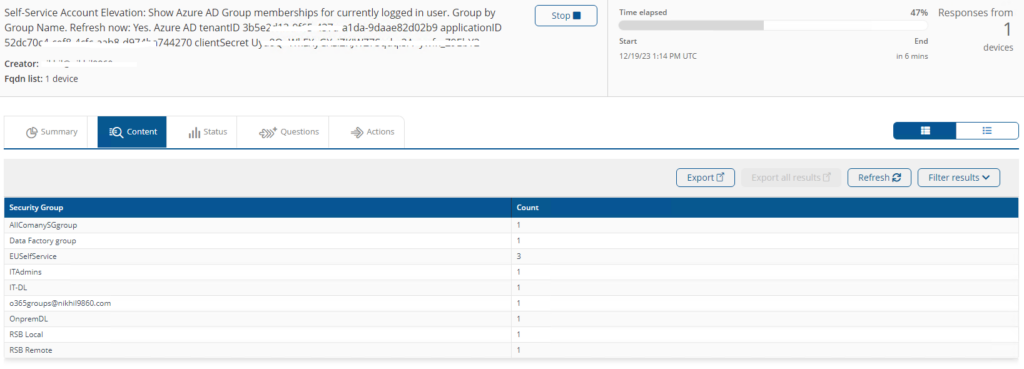
Self-Service Account Elevation: Show Azure AD Group memberships for currently logged in user. Group by Group Name. Refresh now: <Refresh>. Azure AD tenantID <TenantID> applicationID <appID> clientSecret <clientSecret>
This instruction will show Azure AD group memberships for the currently logged in user.
Components
1E-Exchange-Self-Service-MakeAdminOwnPC
Description
Self-Service Account Elevation - used to add a user to a local group on the machine specified.
Readable Payload
Self-Service Account Elevation - Add user %Username% to the Local Administrators group, ONLY ON HOST: %Hostname%
1E-Exchange-Self-Service-WhitelistLocalAdmin
Description
Adds or Removes the user specified to the Admin whitelist which is used to determine what account will be left enabled when Self-Service Account Elevation admin removal functions are run
Readable Payload
Self-Service Account Elevation Whitelist - %Action% user %UserName%
What's New
20 Jan 2025:
>Fixed issue related to multiple user logged-in on a device.
17 Oct 2024:
> Added the multi-language Windows OS support
