Copyright © 1E 2022 All Rights Reserved
OS Supported - Microsoft Windows
Description
This DEXPack (formerly Product pack) contains an Endpoint Automation policy (formerly Guaranteed State). It enables organizations to protect computers and drives against data theft and makes sure that BitLocker encryption is always enabled on Windows devices.
Key Features
- IT departments want to make sure BitLocker is always enabled on managed devices.
Setup
- Upload this DEXPack with the help of the Product Pack Deployment Tool.
- An Endpoint Automation Policy named Enable Bitlocker will be created.
- An Endpoint Automation Rule named Turn on Bitlocker will be created.
- An Instruction Set named Bitlocker containing all the instructions will be created.
Usage
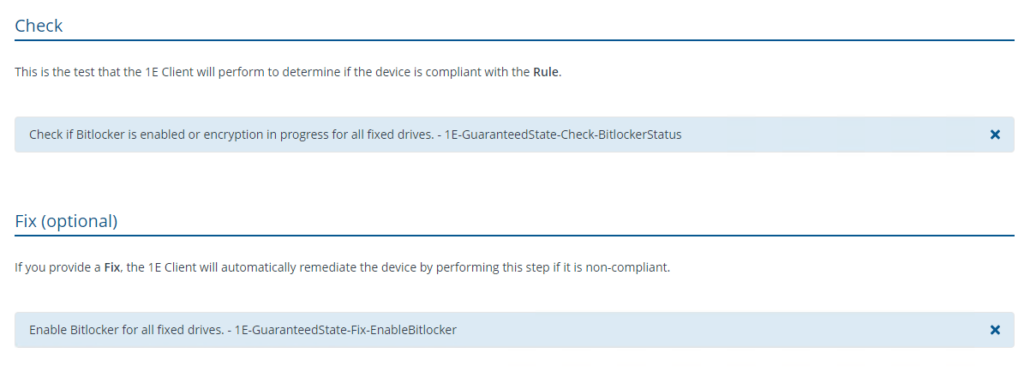
- Review the rule Turn on Bitlocker.
- The trigger is evaluated periodically based on IntervalMinutes to trigger the check and fix.
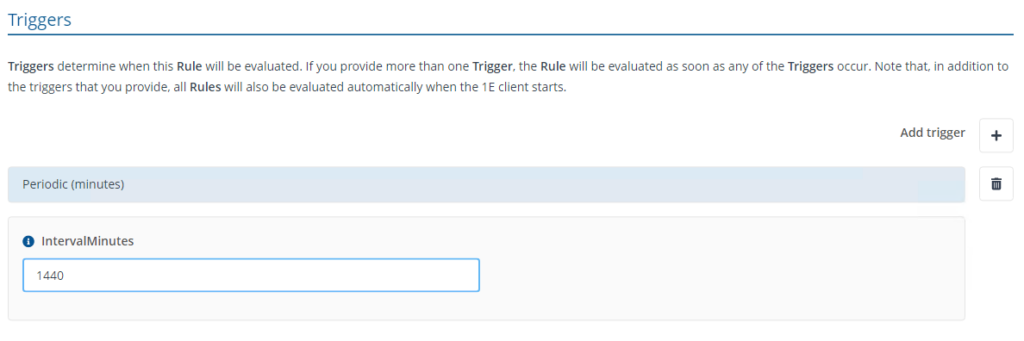
-
The check will evaluate the status of BitLocker on a device. If BitLocker is not enabled, it will trigger the fix to enable it.
Note: BitLocker will be enabled only after the system requirements are met. Visit BitLocker | Microsoft Learn for more information.
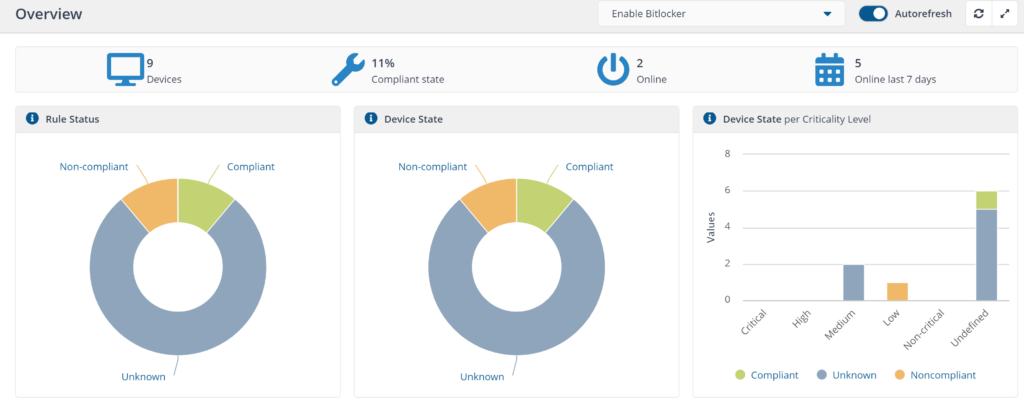
Reports
Reports will start generating a few days after policy is deployed, you can view them using the Endpoint Automation application portal.
Device state definition information by state:
- Compliant - devices where BitLocker is enabled
- Not applicable - devices that do not support BitLocker
- Unknown - devices yet to report their state.
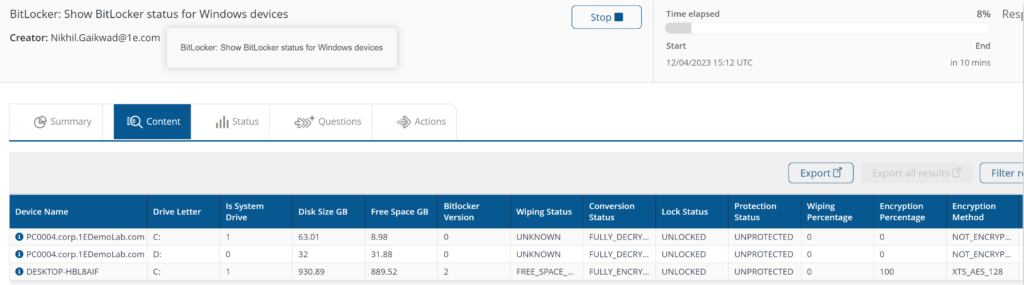
Instruction
BitLocker: Show BitLocker status for Windows devices
Provides information on BitLocker status, including Drive Letter, Encryption Percentage, Encryption Method, Disk Space GB, and Bitocker Version for each volume.
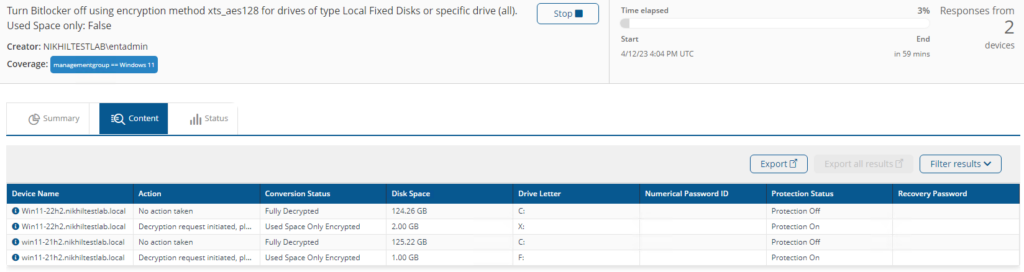
Turn Bitlocker %SetState% using encryption method %EncryptionMethod% for drives of type %DriveType% or specific drive %DriveLetter%. Used Space only: %UsedOnly%
Enables and disables BitLocker on target devices for disk type (Local Fixed Disks, Removable Disks (USB etc.), All (Fixed and Removable)).
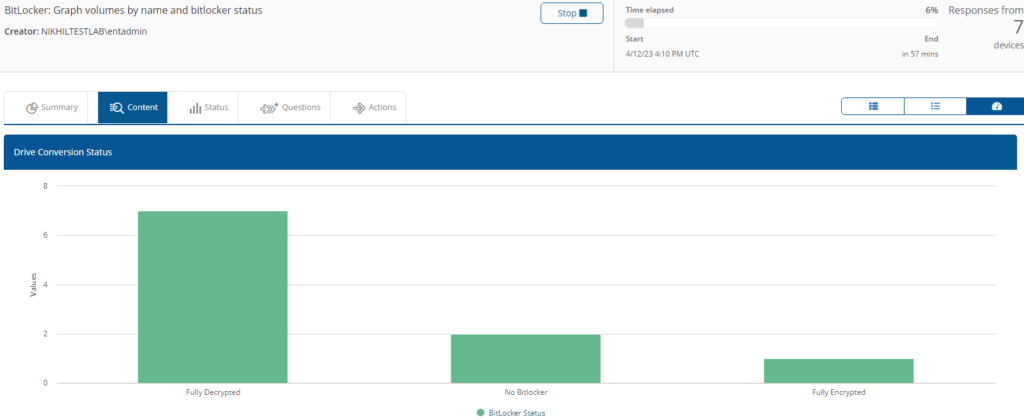
BitLocker: Graph volumes by name and bitlocker status
Provides a bar chart and aggregated information on BitLocker status.
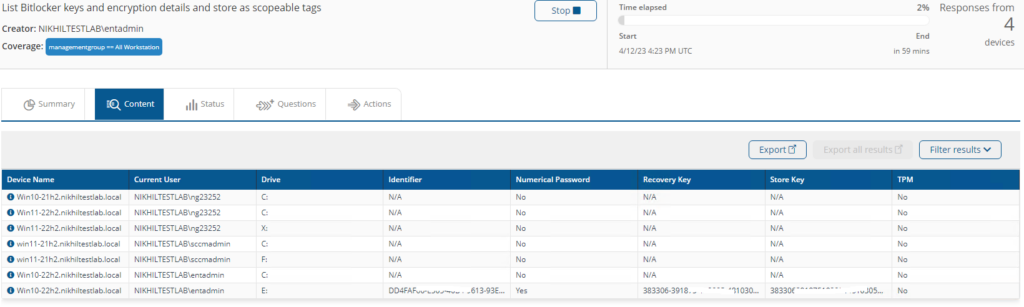
List Bitlocker keys and encryption details and store as scopeable tags
Retrieves BitLocker recovery and store keys, and stores encryption details as scopable tag.
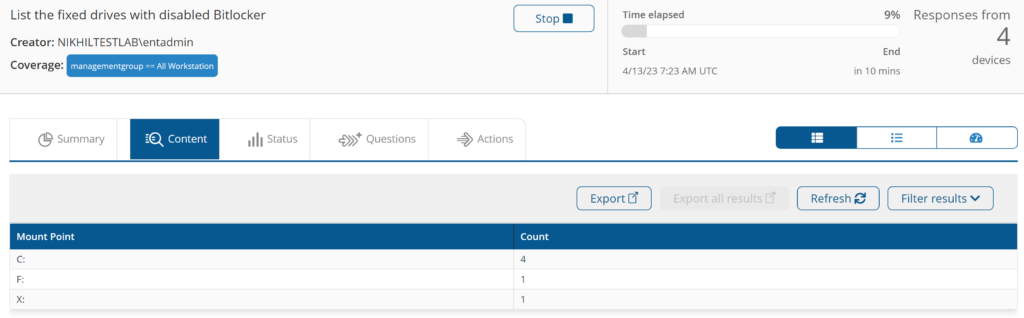
List the fixed drives with disabled Bitlocker
Display the drives for which the BitLocker is not enabled and aggregates the volume name.
Initialize and clear the TPM
Provides TPM status and initializes it.
Bitlocker: Shutdown device and require user to enter recovery key on reboot
This instruction uses the manage-bde command to flush the BitLocker recovery key from the device TPM. It then reboots the device. The user will need the recovery key to reboot and the device will prompt for the recovery key on each reboot from that point on until the companion instruction (Bitlocker: Store BitLocker recovery key in device TPM) which restores the key to the TPM.
Bitlocker: Store BitLocker recovery key in device TPM
This instruction restores the recovery key to the TPM. reversing the effect of the previous instruction (BitLocker: Shutdown device and require user to enter recovery key on reboot). At this point the device will cease prompting for the recovery key on reboot.
Back up the keys for Bitlocker enabled drives
Back up BitLocker keys for enabled drives to Active Directory.
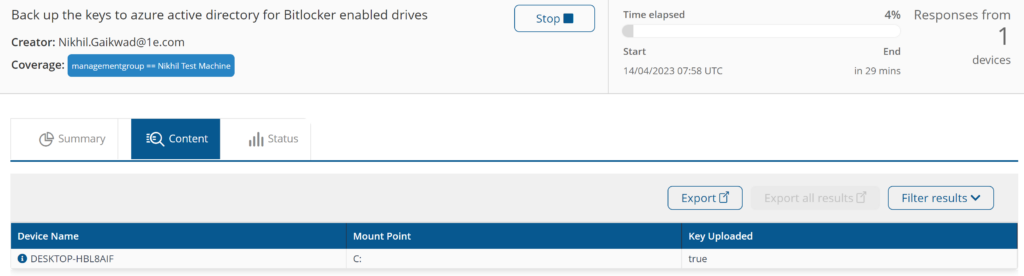
Back up the keys to azure active directory for Bitlocker enabled drives
Back up BitLocker keys for enabled drives to Azure Active Directory.
Components
1E-Exchange-EnableBitLockerTPM
Description
Stores the Bitlocker recovery key in device TPM to enable the Bitlocker
Readable Payload
Bitlocker: Store BitLocker recovery key in device TPM
1E-Exchange-FindNonBitLockerDrives
Description
Display the drives for which the bitlocker is not enabled.
Readable Payload
List the fixed drives with disabled Bitlocker
What's New
21/07/2024:
- Bug fixed (removed the external disk drives from enabling encryptions)
14/07/2023:
- Added support for non-English Operating Systems
